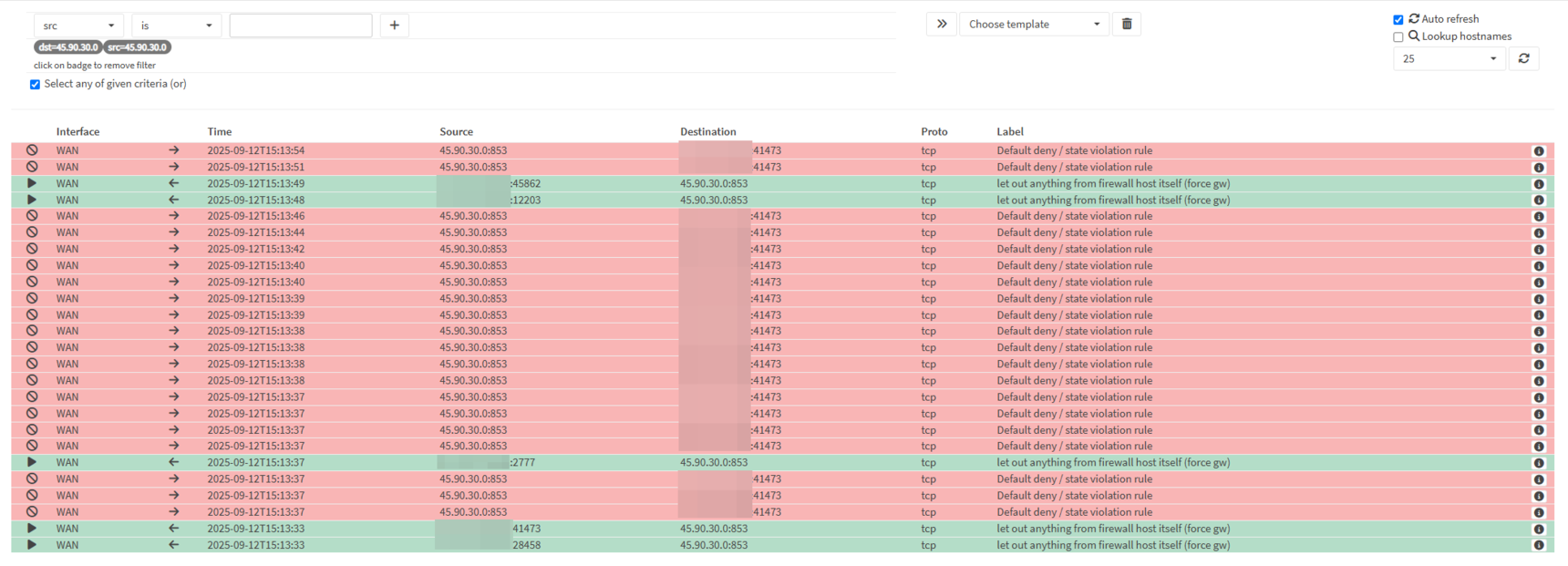
Security Violation - Port Scan by NextDNS
Hello NextDNS,
I just noticed, that my firewall blocked the traffic to your DNS server, as one of your servers tried to port scan my network. The ban was performed by CrowdSec.
Looks like, I'm not the only one noticed being scanned by this IP:
https://app.crowdsec.net/cti/45.90.30.0
May you explain, why you are performing such scans on your users?
Here the output of the cscli, if needed
root@OPNsense:~ # cscli decisions list -m -a -t ban --origin crowdsec | grep 45.90.30.0
| 48771938 | crowdsec | Ip:45.90.30.0 | firewallservices/pf-scan-multi_ports | ban | US | 34939 nextdns, Inc. | 19 | 15m40s | 34963 | localhost |
root@OPNsense:~ # 34963
root@OPNsense:~ # cscli alerts inspect 34963################################################################################################
- ID : 34963
- Date : 2025-09-11T13:13:33Z
- Machine : localhost
- Simulation : false
- Remediation : true
- Reason : firewallservices/pf-scan-multi_ports
- Events Count : 19
- Scope:Value : Ip:45.90.30.0
- Country : US
- AS : nextdns, Inc.
- Begin : 2025-09-11 13:01:00.535888474 +0000 UTC
- End : 2025-09-11 13:02:36.670421869 +0000 UTC
- UUID : beb62fad-36c0-4054-8d88-23590cc87209╭───────────────────────────────────────────────────────────────────────╮
│ Active Decisions │
├──────────┬───────────────┬────────┬────────────┬──────────────────────┤
│ ID │ scope:value │ action │ expiration │ created_at │
├──────────┼───────────────┼────────┼────────────┼──────────────────────┤
│ 48771938 │ Ip:45.90.30.0 │ ban │ 15m19s │ 2025-09-11T13:13:33Z │
╰──────────┴───────────────┴────────┴────────────┴──────────────────────╯- Context :
╭──────────┬───────────╮
│ Key │ Value │
├──────────┼───────────┤
│ dst_port │ tcp:21070 │
│ dst_port │ tcp:51529 │
│ dst_port │ tcp:24948 │
│ dst_port │ tcp:43535 │
│ dst_port │ tcp:3699 │
│ dst_port │ tcp:64590 │
│ dst_port │ tcp:6345 │
│ dst_port │ tcp:6002 │
│ dst_port │ tcp:33976 │
│ dst_port │ tcp:8364 │
│ dst_port │ tcp:2928 │
│ dst_port │ tcp:59117 │
│ dst_port │ tcp:52315 │
│ dst_port │ tcp:51710 │
│ dst_port │ tcp:11476 │
│ dst_port │ tcp:40199 │
╰──────────┴───────────╯
3 replies
-
Is the source port 53 by any chance?
Content aside
- 4 mths agoLast active
- 3Replies
- 190Views
-
2
Following